SaaS has become the operating system of the modern enterprise. Work, data, and automation now live in interconnected apps, APIs, and AI copilots. Each new integration accelerates the business while expanding the blast radius. The traditional perimeter is gone; risk now moves across identities, tokens, and sensitive data flows.
This is why SaaS security is emerging as its own discipline. The job is to see how your environment actually behaves in real time, lock down tenant configurations, govern non-human identities, and control the connections that bind apps together. Success means understanding where sensitive data lives, how it moves, who or what can act on it, and enforcing guardrails without slowing the business.
Vorlon approaches SaaS security as an ecosystem problem. We unify posture management, secrets and token governance, data flow visibility, behavioral analytics, and agentless DLP with automated response connected to the right teams, technology, and workflows. The outcome is resilience at cloud speed: fewer blind spots, faster investigations, and safer adoption of the tools your business now depends on.
What is SaaS security?
SaaS Security is the practice of protecting data, IP, and systems through monitoring and controlling user access, non-human identity (NHI) access, configurations, and integrations across cloud-based Software-as-a-Service (SaaS) applications, where organizations typically lack direct control over their infrastructure.
As businesses increasingly adopt SaaS applications like Google Workspace, Microsoft 365, Salesforce, Workday, GitHub, Slack, and Zoom, their critical data and operations migrate outside traditional security perimeters. SaaS Security has emerged as the discipline and practice of defending this distributed digital environment.
SaaS security typically involves the following:
- Data Protection: Safeguarding sensitive business and customer data stored in SaaS apps from breaches, leaks, or unauthorized access.
- User Access Management: Controlling who can access what within the SaaS ecosystem through identity verification, role-based permissions, and behavior monitoring.
- Non-Human Identity Security: Governing service accounts, OAuth apps, API tokens, bots, and AI agents that operate autonomously within the SaaS ecosystem, including lifecycle management, scope minimization, and monitoring for anomalous behavior.
- Configuration Hardening: Ensuring security settings in SaaS apps are correctly configured to reduce vulnerabilities.
- Third-party Integration Oversight: Monitoring and securing APIs and app integrations that may introduce additional risks.
- Visibility and Control: Providing centralized oversight despite the decentralized nature of SaaS, enabling organizations to detect threats, enforce policies, and respond to incidents.
- Evolving Threat Defense: Staying adaptive to new threats, as traditional perimeter tools (like firewalls or endpoint detection and response) are ineffective in the cloud-first world.
- AI Tools and Agents Oversight: While not typically covered by traditional SaaS security tools, Vorlon views AI agents, tools, and integrations as a critical part of the SaaS ecosystem. This includes discovering and monitoring how they access sensitive data, make autonomous decisions, and introduce new attack vectors.
Ultimately, SaaS Security fills the gaps left by legacy security models, offering the visibility and enforcement needed to protect what organizations rely on most: their people, their data, and their business-critical workflows, in security environments they don’t directly control.
A CISO’s perspective: SaaS security in action
Industry reports and frameworks make the risks clear, but what does SaaS ecosystem security actually look like in practice?
Hear from Anthony Lee‑Masis, CISO of ThoughtSpot, in this short testimonial. He shares how Vorlon transformed his team’s workflow, improved compliance reporting, and helped them uncover risky SaaS behavior in less than 24 hours:
What you’ll learn from the video:
- How Vorlon simplified SaaS ecosystem management and increased team engagement
- Why contextual alerts and automated triage save hours every week
- How real‑time visibility makes compliance with GDPR and other regulations achievable
- Managing third‑party and AI‑driven risks with proactive monitoring
- Why security leaders see Vorlon as a game‑changer for SaaS security
If you’re grappling with SaaS sprawl, compliance headaches, or third‑party vendor risk, this video shows the difference a SaaS ecosystem security platform can make.
Why is SaaS ecosystem security recommended over traditional SSPM solutions?
SaaS ecosystem security takes a wide-angle view, securing not only individual apps but also the entire web of connections between SaaS applications, including sensitive data flows, users, non-human identities, and AI tools. In a world where one misconfigured identity can compromise an entire customer database, this more integrated approach is non-negotiable.
Moreover, modern SaaS environments are built on multi-vendor platforms, API integrations, and cross-app dependencies. That means your security posture is only as strong as the weakest connected service, and how those services interact with each other. Proper SaaS ecosystem security demands continuous monitoring, threat correlation, visibility into data in motion, and anomaly detection to protect against sophisticated attacks.
It’s a far more resilient approach than viewing each SaaS application as an isolated security challenge. This is how you reduce risk, contain blast radius, and protect the integrity of your entire SaaS and AI footprint.
SaaS security components and controls
SaaS security centers on the controls you own inside each tenant and across the ecosystem of connected apps and services. The goal is to protect data and operations by governing identities, configurations, integrations, and data flows.
- Identity and access for humans and non‑human identities (NHI)
- Enforce SSO, MFA, and least privilege with RBAC or ABAC.
- Discover and govern NHIs such as service accounts, OAuth apps, bots, and AI agents.
- Manage lifecycle: provisioning, deprovisioning, key rotation, and applying the principle of least privilege..
- SaaS configuration and posture management (SSPM)
- Continuously assess SaaS tenant settings, external sharing and collaboration policies, and drift.
- Prioritize and remediate misconfigurations that expose data or enable lateral movement.
- Produce audit evidence mapped to frameworks like SOC 2, HIPAA, PCI, and GDPR.
- Integration and API/OAuth governance
- Inventory third‑party apps, API keys, tokens, and webhooks; evaluate risk and scopes.
- Monitor usage patterns and data egress; revoke risky tokens quickly.
- Apply API security basics: strong auth, input validation, and rate limiting.
- Data protection for SaaS
- Apply DLP for SaaS to control sensitive content sharing and external exposure.
- Map where sensitive data lives and how it moves across apps and integrations.
- Quarantine or fix risky links and permissions while minimizing the disruption to operations.
- Activity monitoring and analytics
- Correlate user, NHI, external threat intelligence,and app events to spot suspicious behavior and anomalies such as mass downloads, privilege spikes, or access from unusual geolocations.
- Normalize incomplete vendor logs and enrich signals; forward to SIEM/SOAR for triage and response.
- Secrets and token hygiene
- Centralize storage, automate rotation, and detect leaked or over‑scoped credentials.
- Remove hardcoded secrets and enforce temporary, least‑privilege access.
- Shadow IT and SaaS discovery
- Detect unsanctioned apps via OAuth grants, SSO logs, and network telemetry.
- Classify risk and guide safe adoption or decommissioning.
- Governance, risk, and compliance
- Align controls and evidence collection with regulatory and internal policies.
- Track data residency, retention, and access reviews.
- Incident response and automation for SaaS
- Standardize playbooks for token revocation, session termination, and permission rollback.
- Integrate with ITSM for tickets and approvals to accelerate remediation.
Note on scope: Network, endpoint, and the provider’s runtime application security remain important, but they sit largely outside the customer’s control in SaaS. The strongest levers are identity, configuration, integration oversight, data protection, detection, and response.
How does SaaS security relate to SaaS Security Posture Management (SSPM)?
SaaS security is the broader program to protect data, users, and business workflows across all SaaS tenants and the integrations that connect them.
SSPM is a foundational capability within that program. It continuously assesses SaaS tenant settings, permissions, external sharing and collaboration policies, and drift management to reduce misconfigurations and align with policy and compliance requirements. Most SSPM deployments also track third‑party/OAuth apps and token scopes, surface risky defaults, and provide audit evidence.
How they fit together:
- What SSPM typically covers: SaaS configuration baselines, access and sharing policies, OAuth and app integrations, change monitoring, and compliance reporting. It also complements SIEM/SOAR by supplying posture and context for investigations.
What SSPM does not replace: Data‑in‑motion enforcement (e.g., CASB or secure gateways), endpoint and network controls, or the provider's infrastructure and application runtime security.
The evolving shared responsibility model
The traditional shared responsibility model in cloud security has undergone a significant transformation. According to a recent S&P Market Intelligence 451 Research Report on SaaS Security Posture Management, we're witnessing a "converged destiny" where responsibilities are merging among customers, SSPM vendors, compliance automation platforms, SaaS companies, and the cloud service providers they're built on.
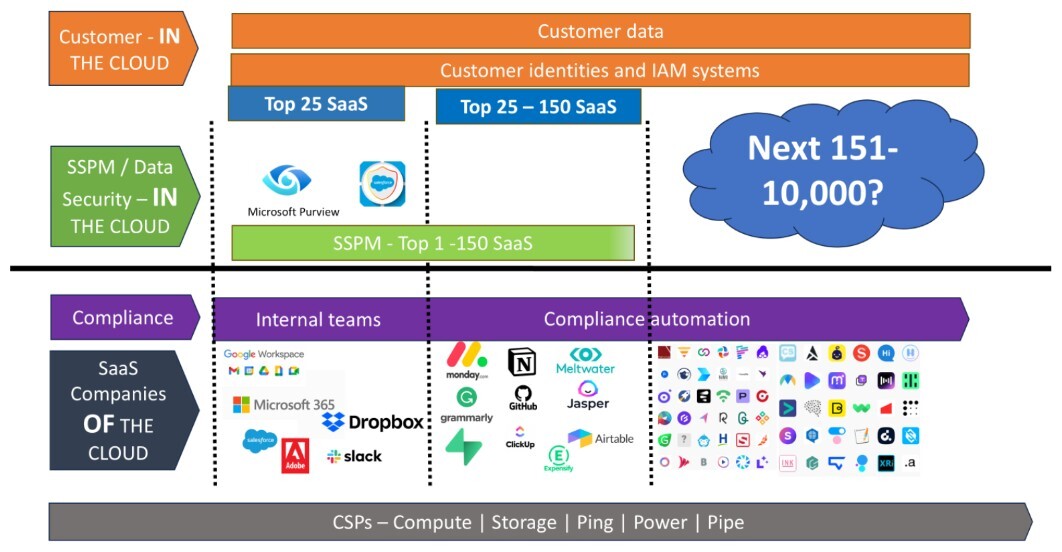
Source: S&P Global Market Intelligence 451 Research
This evolution reflects a fundamental shift in how SaaS security operates. While early cloud models clearly separated "responsibilities in the cloud" from "responsibilities of the cloud," today's reality is far more integrated. From left to right, the diagram illustrates how different tiers of SaaS providers approach compliance and security:
- Top 25 SaaS providers (like Microsoft 365, Google Workspace, Salesforce, Slack) often build their own internal SSPM capabilities
- Top 25-150 SaaS providers increasingly rely on compliance automation to demonstrate secure design
- The next 151-10,000+ emerging SaaS offerings represent a massive challenge for enterprises trying to safely onboard and secure thousands of new services
The report highlights a critical question: Can thousands of SaaS companies ensure their platforms can be operated safely, with customers able to take control of security in the cloud themselves? As generative AI and agentic approaches transform SaaS into "service as software," the need for unified visibility and control becomes even more urgent.
This converging landscape is why Vorlon takes an ecosystem approach to SaaS security, providing comprehensive visibility across the entire interconnected environment, not just individual applications.
Want to see how Vorlon helps security teams secure the entire SaaS ecosystem, not just the top 25 apps? Download our SaaS Ecosystem Security Solution Brief for a concise breakdown of core capabilities and real-world use cases.
The top SaaS security risks, threats, and challenges
SaaS delivers speed, but that speed opens doors. Here are the leading risks that put your data, users, and operations in the crosshairs:
- Unauthorized access: Anywhere access means wider attack surfaces. Without tight identity controls, bad actors can slip in undetected.
- Data breaches: SaaS platforms are a goldmine of data. One breach can expose sensitive corporate and customer information, costing millions and damaging trust.
- Lack of control: You don’t own the infrastructure. That means limited visibility, minimal configuration oversight, and increased dependency on third-party security postures.
- Compliance challenges and gaps: Navigating GDPR, HIPAA, or CCPA across decentralized cloud platforms is complex, and mistakes are costly. Furthermore, Gartner cautions that “SaaS is attracting more attention from threat actors, requiring security and risk management leaders to address critical cybersecurity gaps in this cloud form factor.”
- Data loss: Whether it’s accidental deletion, malicious activity, or provider-side issues, cloud-based data can disappear without the right protections in place.
- Account hijacking: One compromised credential is all it takes. Phishing and session hijacking can grant attackers full control of user accounts.
- Weak authentication and authorization: No MFA. Poor password hygiene. Loose role assignments. These gaps invite exploitation.
- Shadow IT: Unsanctioned SaaS apps bypass IT oversight and introduce unmanaged risk: no policies, no visibility, no control.
- Misconfiguration: It’s not always an attacker; it’s often you. Misconfigured settings are a leading cause of SaaS data exposure.
- Vendor risks: You’re only as secure as your provider. Weak security practices or unchecked third-party integrations amplify your risk footprint.
- Cross-site scripting (XSS) and injection attacks: Exploitable code flaws in SaaS apps can be used to run malicious scripts and exfiltrate data.
- API vulnerabilities: APIs power SaaS integrations, but insecure API endpoints can become wide-open doors for attackers.
The benefits of robust SaaS security
SaaS security pays off in day-to-day operations, not just during incidents. Done well, it protects data, keeps teams moving, satisfies auditors, and reduces rework. Here’s what strong fundamentals typically deliver.
- Data protection: Strong SaaS security keeps sensitive data accessible only to the right people and services, catches risky sharing and misconfigurations early, and recovers quickly with reliable backups.
- Compliance readiness: Aligns controls with regulations and produces audit evidence on demand. Under shared responsibility, the provider secures the service; you secure identities, configurations, and data flows.
- Business continuity: Reduces blast radius from mistakes or attacks, keeps core apps available, and executes tested playbooks when something goes wrong.
- Trust and reputation: Demonstrate disciplined access and monitoring, communicate clearly during incidents, and earn confidence from customers and partners.
- Cost control: Preventing incidents costs less than cleaning them up. Automation cuts manual reviews and reduces repetitive work.
- Improved productivity: Clear access models and safe defaults reduce friction for users and admins, so teams spend less time firefighting and more time shipping work.
- Protection against emerging threats: Watch for changes in tokens, integrations, and app settings; revoke or adjust quickly; and adapt as vendors add features like AI and new plugins.
What are SaaS security best practices?
SaaS security is a living, evolving discipline. Here are the best practices for locking down your cloud apps and data:
- Understand your responsibilities: The shared responsibility clarifies: Your provider secures the infrastructure, but your data, users, and configurations are your responsibility.
- Use strong authentication measures: Multi-factor authentication (MFA) and single sign-on (SSO) aren’t optional. Every login is a potential attack surface, so shut down weak access points and make identity your strongest line of defense.
- Manage user access: Least privilege is table stakes. Audit permissions regularly and don’t let dormant accounts remain active.
- Encrypt everything: In transit, at rest, everywhere. Encryption is your safety net when attackers try to intercept or exfiltrate data.
- Regularly monitor and audit: Spot threats before they escalate. Continuous logging, auditing, and anomaly detection are your early warning system.
- Build policy into your DNA: Your data security policy should be clear, actionable, and enforced, from access controls to incident response.
- Train for the real world: Users are your first line of defense and sometimes your weakest link. Keep them sharp with ongoing security awareness and threat training.
- Deploy smart security tools: Utilize advanced SaaS security solutions for intrusion detection, data loss prevention (DLP), and real-time threat intelligence. Automation amplifies your effectiveness.
- Vendor assessment: Don’t just trust; verify. Assess your SaaS providers for security posture, compliance, and transparency. Compare their best practices to your own instance and make sure you’re effectively utilizing all the security controls your SaaS providers have to offer.
- Backup data regularly: As data volume and dependency on cloud platforms grow, organizations are waking up to a hard truth: without control over their backups, they don’t control their data. However, SaaS vendor backups aren’t enough. Maintain your own, so you’re covered if disaster strikes.
Why Vorlon treats AI as part of the SaaS security strategy
Most SaaS security tools stop at posture checks and user access controls. They don’t account for AI copilots, plugins, and agents that now act with organizational authority in the same SaaS applications your team depends on. Ignoring AI risk creates dangerous blind spots because these tools can:
- Inherit broad permissions across SaaS apps and APIs
- Move sensitive data between platforms at machine speed
- Operate without clear audit logs, making compliance difficult
- Bypass security policies if discovered outside IT’s oversight (so‑called “shadow AI”)
Vorlon takes a different approach. We treat AI as an integral part of the SaaS ecosystem—not a separate category. That means we continuously map both human and non‑human identities, AI data flows, and SaaS‑to‑AI integrations in one unified security model.
This unified perspective allows your team to:
- Detect unauthorized or risky AI usage alongside SaaS activity
- Investigate and respond to threats whether they originated from a person, a bot, or an AI agent
- Prove compliance with audit‑ready reports that include AI‑driven actions
In other words, your SaaS security strategy is incomplete unless it includes AI. Vorlon helps you close that gap.
Hear our CEO Amir Khayat explain this shift during a live NYSE TV interview on the launch of Vorlon’s SaaS + AI security platform:
How does Vorlon help with SaaS security?
Vorlon brings context and precision to SaaS ecosystem security by mapping what others miss. We provide real-time visibility into how applications, users, non-human identities, and data actually interact.
At the core is DataMatrix™: our engine for visualizing app interconnectivity and secure data flow. It tracks every entity and interaction across your ecosystem, flagging behavioral anomalies and threat patterns as they happen.
Vorlon detects threats as they happen. That includes over-permissioned OAuth tokens, dormant secrets, risky automations, and unusual data and identity access patterns. We correlate human and non-human activity to identify abnormal behavior with context, not guesswork.
When action is required, Vorlon integrates with your existing systems to accelerate response. You can revoke access, rotate keys, terminate sessions, or launch full investigations directly from your SIEM, SOAR, or ITSM tools. Learn more about integrations here.
We also close the growing gap between SaaS and AI. As AI agents and copilots begin making decisions and moving data, Vorlon provides unified visibility across both human and machine interactions. Explore SaaS+AI ecosystem security to see how we help manage this emerging risk.
With Vorlon, you don’t need to piece together partial tools or wait for a breach to learn how your environment behaves. You get one platform to monitor, investigate, and respond.
1Gartner Research: Mind the SaaS Security Gaps, 22 July, 2025. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.











